
ComSolutions Inc appreciates everyone’s patience as our Southeastern regional team works through the devastating aftermath of Hurricane Ida. With our regional office located in Covington, LA, many of our employees have spent the past few days cut off or displaced while they get thier families to safety, and into a position were they can resume providing services. We want our clients in the region to know that we are doing everything we can to reposition our technicians and provide outside support to get everyone back up to functional as soon as possible.
We have been working with many of our clients over the past few days to restore services where power is available. If your business is providing services related to the recovery effort, please let us know so that we can prioritize those needs first.
Please feel free to contact us via email csiteams@comsolutionsusa.com or visit the support page to input a support request directly into our system.
Don’t Panic, Stay Safe, and Let Cooler Heads Prevail

As the situation surrounding COVID-19 continues to evolve, many business owners and employees alike are afraid that they will not be able to continue working as quarantine regulations continue to become more strict. As the situation has progressed, we’ve found that most of our clients have been able to stay operational despite quarantines by leveraging to power of modern IT technologies. Here’s how:
Remote Access Technology
Just because you have to stay home does not mean you can not work. One of the biggest concerns businesses have is that they are afraid that there is some piece of software, hardware, etc in the office that they need physical access to in order to function. For the majority of businesses, this is not the case. Services your IT provider should be able to offer to keep you moving forward include:
- Setting up remote connections between home computers and office computers. This way, users don’t lose access to any of the software, settings, or features of thier work machines or networks. Everything you do on your home computer actually happens on your work computer back at the office; so, you maintain 100% access to your digital resources.
- Setting up cloud based software solutions. Nowadays, most general business applications can be done using purely internet based services where your files and programs exist purely online. By moving to the use of Cloud based systems, you may not need to make any special accommodations for remote work. Logging in from home is exactly the same as logging in from the office.
- Setting up a VoIP phone system. While most businesses have already migrated to VoIP phones over the past several years, not all business owners realize the full versatility that these internet based phone systems can offer. In most cases, you can simply forward you calls to a cell phone, or better yet, just take your office phone home with you, and you will be able to continue to take phone calls just like you are back at the office.
- Help you establish alternate business locations and setups. In some cases, there is the issue of needing access to things like printers, scanners, etc. While not everyone knows how to set this equipment up on thier own, it is typically simple enough that your IT provider can walk you through the wiring process by phone, then complete any needed configurations by remote desktop connection should the need arise. This way your home workspaces can be fully established without the risk of human exposure you would normally see from an in-person service call.
- Before you attempt to migrate your business to work remotely, you should always consult with your IT provider first. In many cases, your office setup will include things like power saver settings, firewalls, compliances, or other roadblocks which could result in an interruption of services.
- Lastly, only use IT providers that you already trust. Amid the chaos, many scammers have been using the opportunity to pose as IT support agents to try to gain access to people’s computers. If you receive an unsolicited phone call or email claiming to be from a company that is not your IT provider, hangup/spam them right away.
Strong Customer Engagement
Another key part of maintaining business continuity in this situation may include improving your methods of customer communication to keep your consumers well enough informed to adapt to any changes in your business’s operations. If your IT provider does not offer these services, check with your web developer or marketing company.
- A lot of people will be Googling your business to see if you are still open. It is important that you update your Google Business profiles to reflect any temporary changes in store hours. Not posting accurate times that you will be closed can create a lasting negative impression with your customers.
- Post policy updates to your website and social media pages. People REALLY want to know what to expect when doing business with you right now. Are you closed, are you suspending some services but not others, are you reducing or extending your hours, etc. Even if you are doing absolutely everything as normal, people want to know that too.
- Set up mailing lists and/or auto callers where you can inform clients of changes as they happen.

Spam filters are our friends. They help keep us safe from phishing attacks, money laundering schemes, malicious hyperlinks and viruses, boat loads of unwanted ads for umm… “male performance medications”. We like our spam filters, but sometimes they get things wrong and we need to take extra steps to correct them.
Before we get too deep into this subject, we first want to cover the number one lesson in email whitelisting: MAKE SURE YOU ACTUALLY TRUST THE SENDER!
What I mean by this is that an illegitimate company may try to to convince you to whitelist them for a seemingly benign reason so that they can follow up with a malicious email. If you are doing business with a company that you solicited or you are trying to receive and email that is being blocked from a person you actually know, then whitelisting can help make sure that you receive all the emails you are supposed to be getting. But if an Algerian prince or Microsoft Tech Support randomly contacts you and asks you to whitelist their emails, well that is not a trustworthy source.
Whitelisting Instructions by Email System
In the following examples we will pretend that these emails are coming from the email address example@gmail.com For your own purposes, substitute this email address with whoever you are trying to unblock.
Gmail
- Login to your email account.
- Click the “Spam” link at the bottom of your folders list in the left hand column.
- Click on an email sent by the person or business you want to unblock.
- Click the “Report Not Spam” button above the message.
- To also unblock images, click the green box above your message that says “Always Display Images from example@gmail.com”.
Windows Live Hotmail
- Login to your email account.
- In the upper-right corner of the Windows Live Hotmail home page, click “Options”, and then click “More Options”.
- Under Junk Email, click Safe and Blocked Senders.
- Click “Safe Mailing Lists”.
- Add the email address to the list.
- To also unblock images, open an email from the sender, then click “show content” at the top of the message.
Microsoft Outlook
- Right-click on any message in your Inbox and point to Junk, then to Junk E-mail Options.
- Select the Safe Senders tab.
- Add example@gmail.com to the list.
- This should also unblock images.
AOL
- Login to your email account.
- Go to AOL Keyword: “Mail Controls”.
- Next to Sender Filter, click the “Edit” link.
- Under “My Sender Filter”, click the “Use a Custom Sender List” link.
- Choose the “Block all senders and domains listed below or Allow only the sender and domains listed below” option, then click the “Save” button.
- Click the “Save” button to close the Sender Filter window.
- Click the “Save” button to close the Mail and Spam Controls window.
- To unblock images:
- Click the Mail menu.
- Click Mail Settings.
- Click the “Hide images & disable links in mail from unknown senders” box to clear it.
- Click the “Save” button.
Yahoo!
- Login to your email account.
- Click “Options” at the top right.
- Click “Filters”.
- Click the “Add” button.
- Name this filter, then where it says “From header contains,” put the email address you want to allow.
- Where it says “Then…Move the message to,” select “Inbox”.
- Click “Add Filter”.
- To unblock images:
- go to the “Spam Protection” section and click “continue” until you’re on the 3rd step of the process.
- If you’ve taken the above steps to designate the sender as not Spam, select the “Block images in messages that SpamGuard thinks are spam” option.
Postini Spam Filter
- Login to your Postini Message Center.
- Click “My Settings” in the upper right-hand corner.
- Click “Approve Senders”.
- Add the email address to the Approved Senders box.
- Click “Update Approved Senders”.
SpamArrest
There are two ways to whitelist a sender in SpamArrest.
- Designate them as an Authorized Sender by:
- In the “Members Area,” clicking the “Senders” tab.
- In the field “To authorize a sender enter their email address into the field below,” enter their Email address to designate them as an authorized sender.
- Verify them as an Authorized Sender by:
- In the “Members Area,” clicking the “Mail” tab.
- Underneath “INBOX” in the left hand column, clicking on the folder “Unverified”.
- If an Email from the sender is in your list of unverified senders, check the box beside them in the list and click the “Authorize” button to whitelist their Email address.
OTHER COMMON LIMITATIONS
Business Email Accounts
If you are using an email account provided by your company, it is likely that your IT department is using additional business grade spam filters which you may not have direct control over. You may either need to contact your IT department to whitelist the email address, or use a personal email account instead.
Internet Service Providers
If you are using an email account provided by your Internet Service Provider (Cox, Charter, AT&T, etc.), it is likely that they are using additional proprietary spam filters which you may not have direct control over. You may need to contact tech support at your ISP to whitelist the email address, or use a different email account instead.
HTML
Many emails these days contain at least some HTML. Most email programs can handle HTML including Gmail, Hotmail, MSN, Yahoo! Mail, Microsoft Outlook, Outlook Express, Eudora Pro, Netscape Navigator, Netscape Communicator, Mozilla or AOL 6.0 and up. On the off chance you are using Eudora Light, an earlier version of Eudora Pro, or AOL 5.0 or earlier, you will not be able to receive HTML emails. In some cases, more modern email programs may be set to Text Only mode, in which case, you may have issues reading HTML emails. It is also important to note that most email programs don’t support all HTML; so, an email that does not render well in one, may look much better in another.
Address Book Required
Some Email systems require a sender to be in your address book to keep the Email from being diverted to a “junk” or “bulk” mail folder. If your system has this requirement, add the sender’s email address to your address book.

What is Ransomware?
Ransomware is a kind of virus that prevents you from using your infected computer, phone, or other device. In most cases, it will encrypt your system preventing you from being able to access your files or other aspects of your machine. What sets ransomware apart from other viruses is the fact that it is designed to hold your data hostage and tries to force you to pay a fee to get it back.
Do Not Pay the Ransom!!!
Apart from encouraging criminal behavior, it is common for the attacker to choose not to unlock a machine, even after the ransom is paid.
Rule #1: Never Trust a Hacker.
In modern computing, nearly every security breach begins with a violation of your trust. While not trusting hackers seems like it should be a no brainer, it is important to understand that there are many common lies that a hacker will use to convince you to install malware or to scare you into not telling anyone who might be able to help restore your PC.
The most common cons include:
- Impersonating legitimate businesses to get you to trust them. Microsoft, internet service providers, web hosting companies, email providers, social media platforms, and banks are all common guises used to make you believe that you are dealing with trustworthy correspondence. They use this trust to make you more careless about the software they install, the links you click, and/or the personal information you provide.
- Once installed, ransomware will often claim that you have done something illegal with your PC, and that you are being fined by a police force or government agency. Legitimate law enforcement agencies NEVER use ransomware to issue fines.
- Another frequent scam hackers use are websites, emails, or phone calls that will claim that you have already been hacked. These are usually not true. They are designed to get you to interact with them in ways that will convince you to install fake programs or pay for fake virus removal, but it is often the counterfeit services they are selling which will contain the actual malware.
What can I do to protect myself from Ransomware attacks?
1. Never assume an email is safe:
Do you trust your bank? Facebook account services? How about your friends? The unfortunate truth is that when it comes to email, the answer to all of these questions should always be “no”. There are countless ways a hacker can fake an email to make it look like it came from someone else, and in many cases, when a hacker gains access to someone’s personal email account, they will use that account to issue spam to everyone on their friend’s list to piggyback on that person’s trusted status.
This does not mean that every email is dangerous, but that you should always exercise due caution with every email that you open.
2. Double-check the content of the message.
There are usually errors or discrepancies that you can spot such as a claim from a bank or a friend that they have received something from you. When in doubt, you can check your recently sent items to verify their claim.
Another tell-tale sign is that fake emails from businesses will often begin with things like “Dear Valued Customer” instead of your actual name.
3. Never open links or file attachments in email
In general, clicking on links in email should be avoided. It is safer to visit any site mentioned in email directly. If you do not know a company’s URL off-hand, use a search engine such as Google or Bing. NEVER follow a link in an email asking your to reset a password that you did not specifically request to have reset, since these are often tricks designed to steal your credentials.
Messages can also contain dangerous file types such as zip, exe, php, html, docx, etc. If you do not recognize a file extension, HERE is a pretty good resource for seeing if it is safe or not. If you ever need to receive a potentially dangerous file type, always confirm with the person that they are the ones sending it.
4. Never click on ads offering free software
These scams generally fall into one of 3 categories.
- Pop-ups claiming that you have been hacked, or that your computer is unprotected. These will try to give or sell you fake antivirus software designed to infect your machine with malware.
- Free games, apps, software upgrades, driver scanners, and other various programs are often bundled with malware that could include anything from malware.
- Cracked/Pirated programs are often bundled with malware. These can be especially malicious because the installation instructions included with them will often instruct you to turn off your anti-virus software while it downloads or installs giving it free reign over your machine.
5. Use a reputable Antivirus security suite
It is always a good idea to have both anti-malware software and a software firewall to help you identify threats or suspicious behavior. Malware authors frequently send out new variants, to try to avoid detection, so this is why it is important to have both layers of protection. Most malware relies upon remote instructions to carry out their misdeeds. If you run across a ransomware variant that is so new that it gets past anti-malware software, it may still be caught by a firewall when it attempts to connect with its Command and Control server to receive instructions for encrypting your files.
6. Backup important data
While many older ransomware viruses can be unlocked using the right anti-virus programs, newer ones usually can not. This is why it’s important to have a good backup plan which can vastly minimize your risk of lose. When it comes to backup and recovery, there are many options to choose from and not all of them are made equal. Some backups may only collect certain kinds of files, or files located in certain places. Some backups may be very complete, but take a very long time to restore if things go wrong. So, it is usually best to refer to your IT provider for advice on the best course of action for your organization.

Google, once again, is excited about social media. But not in the ways you might think; this isn’t about another in a failed string of chat apps, or the knockout success that never was in Google Plus. Instead, it’s an entirely new way of recognizing human faces, and one made possible by — you guessed it — creeping on your social media profiles.
In a recently approved patent, Google detailed a system of “Facial Recognition with Social Network Aiding.” It’s exactly what it sounds like, an attempt to parse social connections as a way to better identify your mug.
We don’t shill.
Reverse Image Search works by attempting to match visual cues in photos with other, similar photos. It works mostly as intended, with some results being dead-on, and others complete misses. But as long as the photo is well-lit, and is of a high enough resolution, Google usually nails it.
Its a system that works, but could use improvement. Sometimes the results are only semi-relevant, and for those who don’t have as much data to pull from, it often overlooks matches entirely. Grab your friend Katie from middle school’s Facebook photo, for example. Chances are it only returns the Facebook account using the photo.
But the new system envisions a world where artificial intelligence would identify faces using not only visual cues, but various forms of data from personal communications, social networks, collaborative apps, and even your calendar.
It’s like this
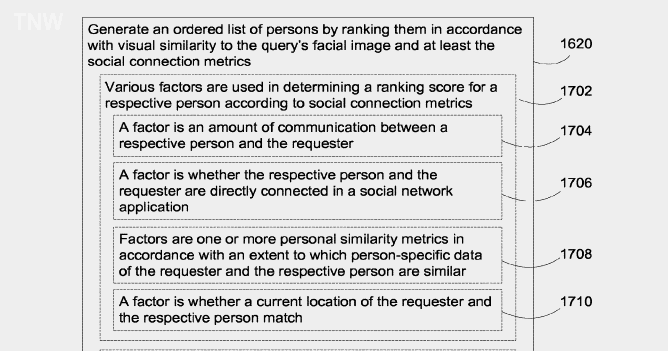
Users enter a “visual query” in the form of a photo, screenshot or scanned image. The system would then analyze the image and look — using advanced image recognition — for others that are both visually similar, and a potential match using the data sources mentioned above.
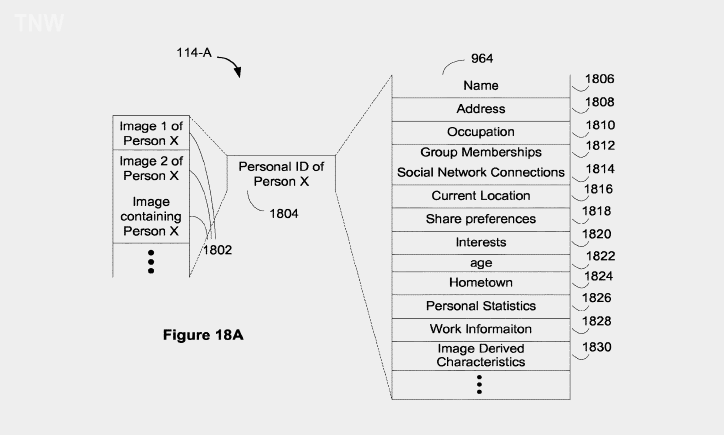
Rather than just matching based on visual cues — Google‘s current system — the software would take additional steps to build further confidence in the person’s identity. Pulling from a number of data sources, including your hometown, age, occupation, and various others, Google would strive to be absolutely sure it returns images relevant to your query, based partially on the data it pulled from your social accounts and other collaborative apps.
Let’s attempt to wrap our head around this with a real example. Inputting an image of Amanda, from accounting, for example, should lead to relevant results with the new software due to a number of connections between you, the searcher, and her, the subject of your search. You’re connected by your employer, you’re friends on Facebook, and she routinely retweets you on Twitter. To Google, these all build confidence that Amanda’s image is indeed the one you’re looking for.
Or maybe you’d search for a childhood friend, Jeff. The same reasoning follows: you’re connected by your hometown, your high school, and an approximate age range.
Where the patent falls short is in detailing exactly how Google would use the technology. We can be fairly sure that Reverse Image Search and Google Photos would benefit. The latter, due to some wording that describes automatically sharing a group photo and tagging everyone in it.
But it’s other, less obvious use cases that could be worrisome. If Google were to bring back Glass, for example. Or if it were to reverse course and continue to provide artificial intelligence to the military. If you’re looking for a tinfoil hat example, that exists too; Google could begin feeding this data to law enforcement, like Amazon.
Rekognition, Amazon‘s feature-rich AI, provides real-time facial recognition to a handful of police departments in Orlando, Florida, and Washington County, Oregon. It’s not difficult to envision a competing product from Google.
The patent does note that in certain scenarios — scenarios Google fails to define — a person would have to opt-in to have their identify appear in these results. For now, it appears that we’re in the clear. But since this is only a patent, and not working software — to the best of our knowledge — things could change quickly.
It’s something to keep an eye on, but we certainly wouldn’t lose any sleep over it. At least not yet.
Source: thenextweb.com

There are a few common problems in the IT world that you just see over-and-over again to the point that many users are quite familiar with them. Some of them are intuitive like a password lock out or a bad update where you experience a problem, your IT guys tells you what it was, and it pretty much makes sense. And then there are caching errors…
What is a Cache and Why Does My Computer Use Them?
A cache is a small section of memory or disk space reserved to in some way allow a program to run faster. If you think of your filing cabinet as your computer, it’s full of all sorts of documents that you may almost never look at, and then there are those documents like birth certificates and social security cards that you need much more often; so, you put them in a special folder at the front so you can find it quickly every time. If you do this, then you’ve created a kind of cache.
Another way caches work is to store data that’s already been processed so that you don’t have to reprocess it every time you need it. This is like keeping a copy of your completed taxes. If you have all your w2s, receipts, etc. you COULD redo your taxes from the original data if you ever had to provide a copy of them for any reason, but it is far more convenient to just hang onto that finished document. This is another kind of cache.
How do Caching Errors Happen?
So far, caching sound like some organizational no-brainer, and mostly it is, but why do they cause problems? That boils down to things changing how you don’t expect them to. If you think about the first scenario, imagine that you started taking lots of documents from everywhere else and putting them in your cache. This would eventually make your cache take just as long to look through as if everything was normally sorted; so, the thing designed to speed you up may actually slow you down. Like this, sometimes a program may start to consume large sums of memory and greatly slow down after prolonged usage because it just keeps hanging on to more and more.
The second case where you are holding processed data is especially great for speeding things up, but what happens when the information you derived your cache from changes? Maybe you filed your taxes, then realized you have an extra tax form you forgot to include. Now all those processed tax forms are no longer relevant and your taxes must be reprocessed. When this kind of caching error happens, you need to “clear your cache” which is like telling the computer to go double check the original documents and reprocess everything.
 With the average American spending 10+ hours a day plugged in, eye health is becoming an increasing concern in our nation. Recent studies show that between 50% and 90% of people who work at a computer screen exhibit at least some negative symptoms as a result.
With the average American spending 10+ hours a day plugged in, eye health is becoming an increasing concern in our nation. Recent studies show that between 50% and 90% of people who work at a computer screen exhibit at least some negative symptoms as a result.
TVs, Computers, Cell Phones, Tablets, and other screened devices have all become such integral parts of our professional and personal daily lives that many of us would not even consider living without them at this point… but the negative impact they can have on one’s well-being should not be ignored.
Understanding CSV – Computer Vision Syndrome
Computer Vision Syndrome isn’t one specific problem. Instead, it includes a whole range of eye problems including eye soreness, headaches, blurred vision, dry eyes, and neck and shoulder pain. Likewise, there is no one cause for these symptoms. While many people assume the issue is just THAT they are using their devices too much, experts have determined that many of these symptoms can be negated through better habits and understanding of where these issues are coming from. If you suffer from from the above issues, try following these helpful steps:
- Adjust your lighting: The high contrast between a bright screen and a darker room can create extra strain on your eyes. A well lit room allows your pupils to dilate to the appropriate level for your monitor’s light output, or if your device offers the option, make sure to enable low-light mode and/or blue light filtering whenever you are in a more poorly lite enviornment. This can save your battery life and your eyes.
- The 20-20-20 rule: When you are working (or playing) in front of a screen for extended periods of time, take regular breaks for your eyes. It’s not hard once you get into the habit. Every 20 minutes you spend looking at a screen, stop to look at something else that’s at least 20 feet away for at least 20 seconds. On a related note, this is not a bad time to get up and walk around, and just let all your other muscles limber up a bit as well.
- Purchase computer glasses They are like reading glasses specifically for computer screens.
- Reposition your monitor: Monitors should be positioned 20″-30″ away whereas TVs should typically be 8-12 feet away depending on the size of your screen. Also make sure that your eyes are on level with your screen. The neck strain and headaches associated with CSV often comes from poor posture resulting in prolonged periods of looking either up or down with your whole head.
- Break up and reduce your total screen time: If your job requires you to look at a computer for eight hours a day, don’t start playing computer games the minute you get home. Spend more time outdoors, and focus on more distant, real-world subjects.

Many people think of cyber security as a specialized skill set handled by that one smart guy you hire to handle it, but as the world progresses, we find that you can’t just rely on someone else to be your sole gatekeeper for your entire computer system. As cyber-security experts have gotten better and better at making secure systems, criminals have gotten equally better at targeting the weakest link in these systems. And in today’s world, that link is typically the end-user.
The Risk of Not Knowing Cybersecurity Best Practices
When you check your email, it is up to you to decide if and email is fraudulent before clicking on any links. When you are on the web, and you are asked to enter a credit card or other personal information, it is up to you to know if the website you are connected to is both secure and legitimate. When you download an app, you have to decide if the permissions that app is requesting are actually things the app needs or if there is an underlying trojan trying to get the privileges it needs to bypass the security features built into your device. When you get a phone call warning you of a problem, you need to decide if the person you are talking to is actually your service provider, or someone trying to get you to divulge sensitive user account info.
Not knowing how to make these choices can be disastrous. One bad click, is all it takes to get your entire network encrypted by ransomware or install spyware that steals all your passwords.
Making IT Services and Personal Responsibility Work Together
This where your IT consulting firm comes in. If you have not received a Cybersecurity Policy from them request one. For most organizations, this should include:
- Criteria for evaluating if an email, website, link, or application should be trusted.
- Restrictions on what websites and services you may access from your work machine.
- Restrictions on what information can be saved and transmitted under various circumstances.
- Protocols for defining what information is confidential, and how to handle its storage and transmission.
- Instructions for identifying security redflags
- A policy for ensuring that employees are regularly trained on emerging security threats.

October 16th 2017, US-CERT publicly disclosed a vulnerability at the core of the WPA-2 encryption protocol. This vulnerability affects nearly every modern encryption configuration used for transmitting information across the internet, especially Linux and Android devices. The KRACK exploit was discovered by security researcher Mathy Vanhoef before it could be implemented for widespread misuse; however, now that this issue is public knowledge, it is extremely important for businesses to update their systems to protect against it.
How Serious is this Vulnerability?
In terms of how harmful this exploit can be, it is extremely serious:
- It can be used to steal any encrypted information that is transmitted from or received by your computer or mobile devices.
- It can be used to inject various forms of malware into local networks and website.
- It affects all kinds of internet enabled devices; however, the most serious threats of injection are specific to Linux and Android.
The good news here is that a hacker needs to be within range of someone’s wifi network to implement it; so, the likelyhood of it being used against your home computer is fairly low. The most likely candidates for this attack are big businesses and smaller businesses that handle secure information.
Due to the potential damage that this exploit could cause, we strongly urge our clients to review their local networks to ensure that all of their connected devices are properly patched.

Equifax revealed on Sept 7th, 2017 a data breach that compromised the personal information of 143 million users. This breach is reported to have exposed a number of sensitive pieces of personal information including Social Security numbers, birthdays, driver’s licenses, credit card numbers, and credit dispute documents.
To find out if your information has been compromised, visit:
https://www.equifaxsecurity2017.com/potential-impact/
What to do if you’ve been compromised?
- Check your bank and credit card statements for suspicious charges.
- You should make a habit of this. Many hackers wait months or even years to use your stolen information.
- Take an inventory of your online services that may be linked to your bank account or credit card.
- Make sure each account is using a different password to isolate breaches if they occur.
- Make sure you know what services you do and do not actually have so that you can better recognize fraudulent charges.
- Check your credit report for unexpected activity. Equifax is offering one free year of premium tracking to help users stay vigilant of issues that arise from this breach.










