With the increase in frequency of Malware and Ransomware attacks over the past few months, we felt the need to make our clients aware of this threat and offer a best practices summary to assist our clients in defending their networks.
What does it look like and how does it work?
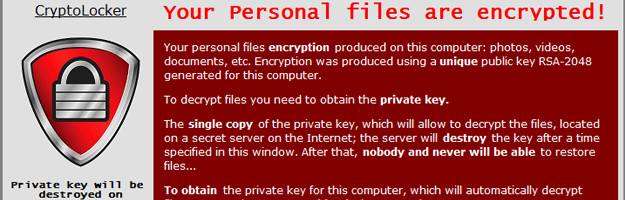
There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC.
They can:
- Prevent you from accessing Windows.
- Encrypt files so you can’t use them.
- Stop certain apps from running (like your web browser).
They will demand that you do something to get access to your PC or files. We have seen them:
- Demand that you pay money.
- Make you complete surveys.
Often, the ransomware will claim you have done something illegal with your PC, and that you are being fined by a police force or government agency. These claims are false. It is a scare tactic designed to make you pay the money without telling anyone who might be able to restore your PC. There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.

Prevalent ransomware
Crowti (also known as Cryptowall), and FakeBsod are currently the two most prevalent ransomware versions. These two families were detected on more than 850,000 PCs running Microsoft security software between June and November 2015.
Please remember once your files are encrypted, you cannot recover them but must restore a fully tested backup and also have removed the threat from your entire system and server.

What can I do to protect myself and my company?
- Always verify who the email sender is:
If the email is coming from a bank, verify with your bank if the message is legitimate. If from a personal contact, confirm that they actually sent the message. Do not rely solely on trust by virtue of relationship, as your friend or family member may be a victim of a virus or spam campaign. - Double-check the content of the message.
There are usually errors or discrepancies that you can spot such as a claim from a bank or a friend that they have received something from you? Try to go to your recently sent items to double-check their claim. Such spammed messages can also contain an executable (.EXE) or ZIP file attachments. Never open .EXE, PHP, HTML or script file attachments within an email. Always confirm with the sender that any ZIP attachments are also legitimate. - Refrain from clicking links in email.
In general, clicking on links in email should be avoided. It is safer to visit any site mentioned in email directly. - Refrain from clicking pop up ads on websites offering software upgrades.
In general, clicking on popups should be avoided. You can contact the software vendor’s website or CNC to obtain an updates necessary for your software. - Use a reputable Antivirus security suite.
It is always a good idea to have both anti-malware software and a software firewall to help you identify threats or suspicious behavior. Malware authors frequently send out new variants, to try to avoid detection, so this is why it is important to have both layers of protection. Most malware relies upon remote instructions to carry out their misdeeds. If you run across a ransomware variant that is so new that it gets past anti-malware software, it may still be caught by a firewall when it attempts to connect with its Command and Control server to receive instructions for encrypting your files. - Backup important data.
Unfortunately, there is no known tool to decrypt the files encrypted by ransomware. One safe computing practice is to ensure you have accurate back-ups of your files. You will also need to ensure all data is being saved properly and guarantee your backups validity. Please contact CNC for your data backup options right away.
CNC advises that you do not pay the ransom
Paying the criminals may never get your data back. There have been plenty of cases where the decryption key never arrived or where it failed to properly decrypt the files. Plus, it encourages criminal behaviour.
We want to discuss the importance of having server images and solid backups of all data. This is the single most important part of your defence. CNC would like to review and verify the type of data backups you are currently using and then discuss our findings in detail. CNC will be reaching out to schedule an appointment and we would be glad to provide you with updated options for your system.

